
Archives
Here are all the past articles.
OWASP
I: Abuse of FunctionalityII: Exploitation of Authentication
III: Injection
IV: Injection Part II
Data Forensics
PhotorecWindows
Kali
NiktoJohn the Ripper
Shred
Burp Suite Set Up Tutorial Small Intruder
I: Wireshark
Web App Vulns
SubdomainsBaker's Dozen
Etcetera
One Time PadPHP Backdoor File Analysis
Hiring Procedures
SPF and Email Spoofing
Photorec in Kali
Grabbed a used laptop hard drive and now I'm going to teach you fools how to carve files and restore their goodlyness.Here are the authors of this tool
www.cgsecurity.org
It is available for Windows, Man, and Linux.
Tutorial will be in Kali Linux.
I'm poor and don't have a usb to sata cable so I'll map it through VMWare to my Kali image.
After Kali boots up, mount the drive
mount -t ntfs /dev/sdb2 /mnt/sdb2Next we will make a place to house the carved files
mkdir /tmp/carvedPull up photorec.
photorecYou will get a screen like this, with a drive selection. I pick the laptop hard drive.
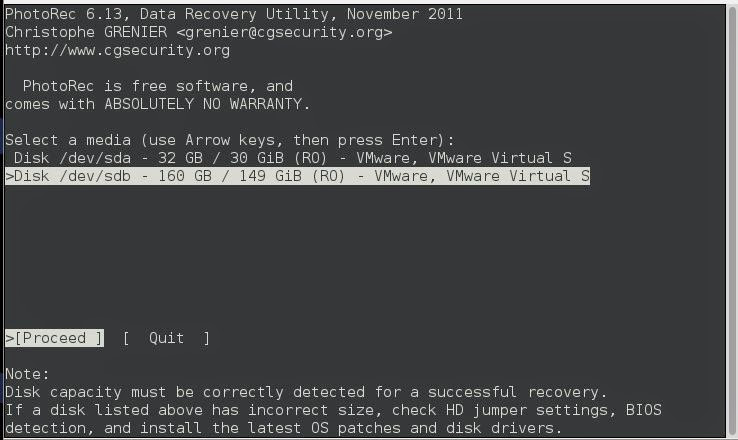
Next screen is where we can select which partition on the disk we want to dig into. It is also where we get into some important settings. (Options, File Opt)
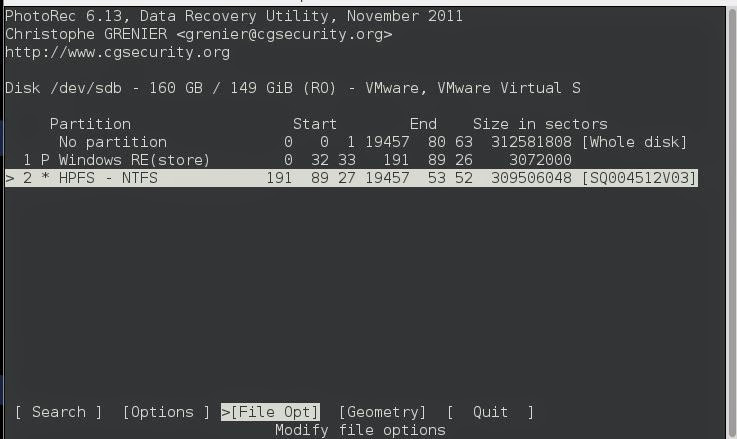
Inside the Options menu, you'll see these few. Personally I think the 'Keep corrupted files: Yes' is the most important, it is No by default, but this is where we can get our deleted information.
Set up the options how you want, then hit quit, it brings you back to the Main Menu.
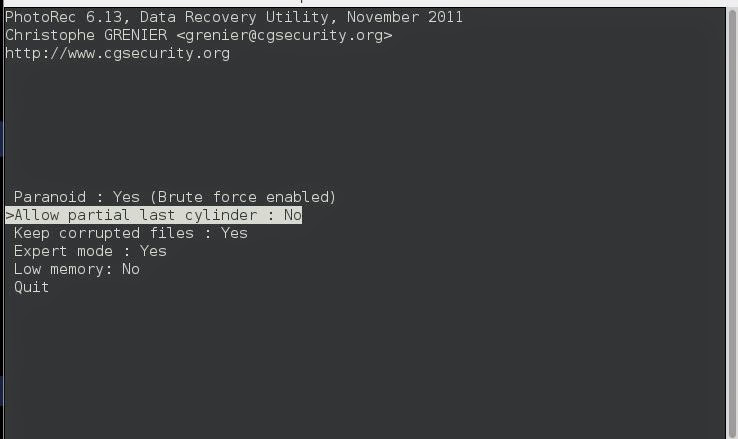
Inside the File Opt menu you have a big list of all the support files that photorec can recover.
These are the file types that photorec has the metadata information for and knows how to recognize them by the file signature.
I only select the Microsoft Office as I am using a virtual machine and don't have much storage.
Pick a directory where you want photorec to put its findings.
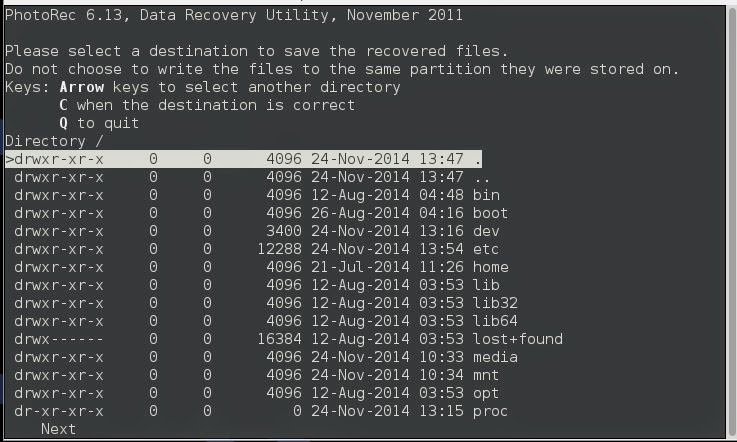
Here you will pick the block size. The default for NTFS is 4KB, so we will leave it at that. If you want to read more about that check Here
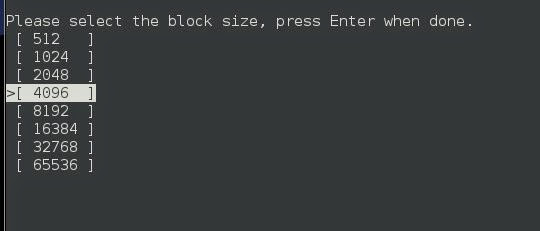
Now you'll pick if you want only Whole files or Partial files, since we are digging for deleted items, we want the data that is in the Free space.
Go get coffee, cause it will take a while to run.
...........................
...........................
Several 'little bits' later
...........................
...........................
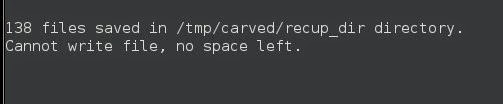
So lets see what we have gotten!
root@kali:# cd /tmp/carved
root@kali:/tmp/carved# cd recup_dir.1
root@kali:/tmp/carved/recup_dir.1# ls -ltr -S
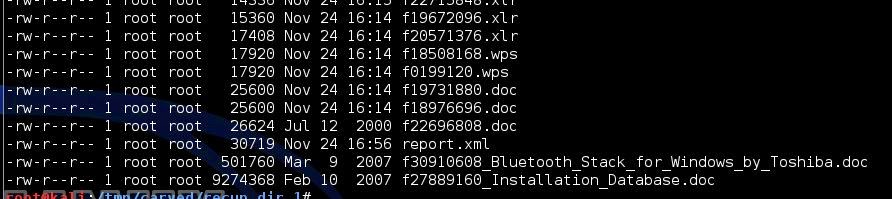
Now, I dug through these files and didn't find anything of interest, so I went back and changed a few options and started another search so we could have an example of something fun to pull from a disc.
I stopped it after 1000 files where pulled.
First thing to grep for is this
Here you are using the power of Regular Expressions to Social Security numbers:
grep -nr "[0-9]\{3\}-[0-9]\{2\}-[0-9]\{4\}" .Grepping for credit card numbers:
grep -nr "[0-9]\{4\}-[0-9]\{4\}-[0-9]\{4\}-[0-9]\{4\}" .
grep -nr "[0-9]\{4\} [0-9]\{4\} [0-9]\{4\} [0-9]\{4\}" .You can use regular expressions to find anything particular that you are looking for.
I didn't find anything too fun on this drive, but I did find out this user had a Fate manual.
-----------------------------------------------------------------------------------------------------------------
-----------------------------------------------------------------------------------------------------------------
-----------------------------------------------------------------------------------------------------------------
Why is it possible to find old deleted files?
A kindergarten explanation and a kindergarten example.
When a file is written onto a hard drive it is going to take up an amount of physical space.
Imagine each bit (1 or 0) takes up one centimeter off disk space.
And imagine a file takes up 2 meters of disk space, starting at a particular address.
When a user deletes a file, the computer just marks the space as available to be overwritten, it does not actively destroy all of the data.
If none of the 2 meters of data is not overwritten, then the entire file can be reconstructed, even though a person cannot see it when using the operating system.
If the first meter is over written with a different file, then the last meter of the old file is still available. This is known as latent data. Even though it is not the full file, it could still contain evidence or sensitive information.
