Archives
Here are all the past articles.
OWASP
I: Abuse of FunctionalityII: Exploitation of Authentication
III: Injection
IV: Injection Part II
Data Forensics
PhotorecWindows
Kali
NiktoJohn the Ripper
Shred
Burp Suite Set Up Tutorial Small Intruder
I: Wireshark
Web App Vulns
SubdomainsBaker's Dozen
Etcetera
One Time PadPHP Backdoor File Analysis
Hiring Procedures
SPF and Email Spoofing
John the Ripper
Because there needs to be at least one more John the Ripper tutorial out there.Author page: http://www.openwall.com/john
This is probably one of the most ubiquitous programs for cracking passwords out there, but I'll try to go into a little more detail than the average JTR tutorial.
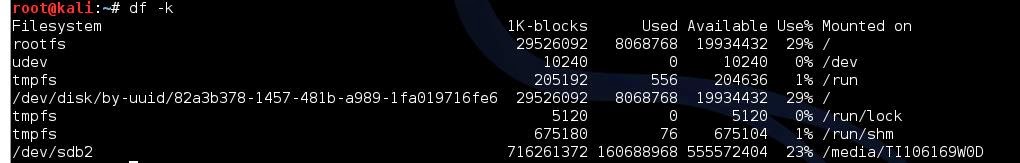
df -k to figure out where the drive wentLooks like it already popped up.
Point yourself to
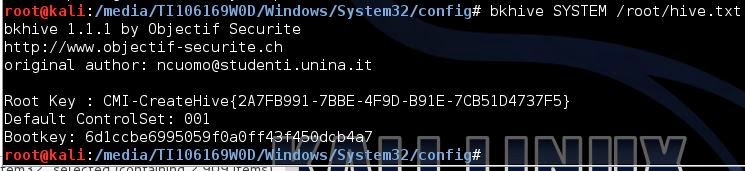
windows/system32/configbkhive system /root/hive.txtbkhive is used to extract the system's boot key.
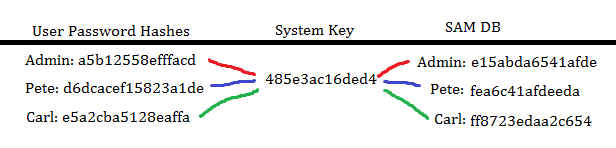
To each iteration of Windows is a unique boot key that is used to encrypt a different set of hashes created by the user passwords before they are stored in the SAM database.
Try and read that sentence again while looking at the graph. Then it might make sense.
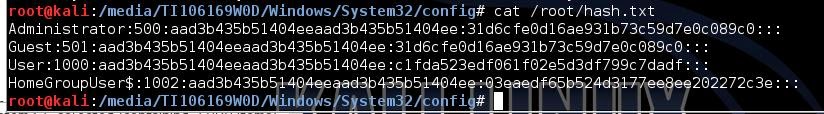
samdump2 SAM /root/hive.txt > /root/hash.txtThis uses the system key we got above and the SAM database to reconstruct the user created hashes.
Here you can see the output
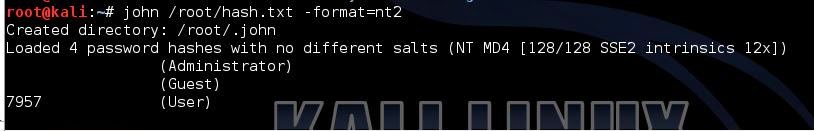
john /root/hash.txt -format=nt2Now to kick off John The Ripper and wait for results.
You can see that it created a directory at
/root/.john you can monitor john.log while you wait for the results to appear in john.pot Like so many others, this password popped in less than a second, a four character password, all numeral.
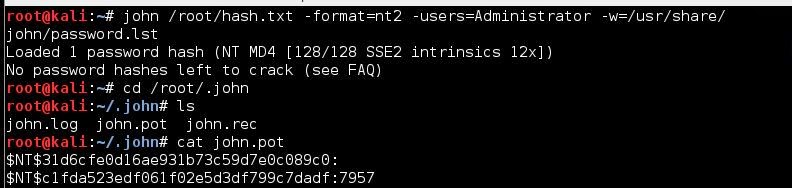
Please note the alternate john prompt. I have added the options -users and -w, short for wordlists.
You can specify for john to only work on one user account, and you can use custom wordlists to help speed up the process.
Dictionary > Brute Force.